Stalkers People You May Know Facebook
We have good news, y'all volition non demand a lot of technical experience to manage to violate a social network, it will exist easier than y'all imagine. Just follow these steps.

Caption to Hack Facebook from a cell phone
- Click on the three dots in the Facebook app
- Copy your victim'south link
- Go to the department on hacking Whatever Social Network
- Paste your victim's link in the box
- Finally, hitting Hack.
Practice you want to learn how to hack all social networks? Then you are in the right place considering nosotros teach you lot to:
- How to hack Facebook.
- How to hack Instagram.
- How to hack Messenger.
- How to hack WhatsApp.
- How to hack Tiktok.
- How to hack Snapchat.
- How to hack Gmail.
- How to hack Youtube.
- How to hack Hotmail y Outlook.
- How to hack Kwai.
- How to hack Telegram.
- How to hack Skype.
- How to hack Twitter.
- How to hack OnlyFans.
- How to hack Tinder.
- How to hack Pinterest.
- How hack an email.
- How to hack Linkedin.
- Track Mobile.
- How to hack Wifi.
Social networks They are incredibly popular platforms these days, as through them we can communicate with people globally.

Hack an account countersign Through specialized software it is so easy, you just need the right key. And here nosotros volition teach y'all some of the methods to achieve it.
Hack social networks through Exploit - Phishing method
Did yous know that by creating and designing a clone folio of the social network of your choice yous tin can get the access data of whoever you want?
Hack with Xploit
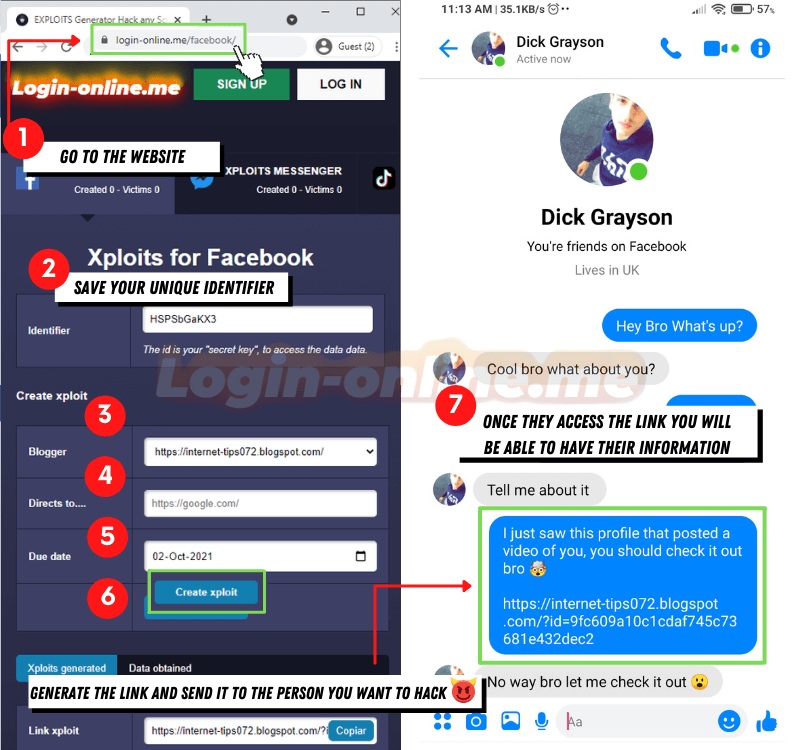
Nosotros summarize the steps in the previous image:
1️⃣ Enter the website https://login-online.me/. And choose the social network you want to Hack
2️⃣ Save your identifier since that is where you can see your victims.
3️⃣ Choose a blogger from the ones that there are, they last very little, This is why many choose to get a premium blogger.
4️⃣ This section is for your victim to enter their data to see a motion picture, a song or whatever you want to put.
5️⃣ The expiration date is until the day the xploits you created volition end working.
6️⃣ Finally create your blogger, we recommend that you start try it before sending it
7️⃣ Send your victim through Facebook, WhatsApp, Email with something striking so that they tin can open it and enter their data.
Brilliant! One time you accept fallen into your trap and provided the requested data, then, go back to the spider web and you will see the data that you have entered there.
The Phishing method it is totally true, through which hackers transport their victims, inviting them to enter a forged link that redirects them to a chief page of their social network, totally the same every bit the original, so that they enter their login data.
Spy apps to hack a social network
Today, anyone tin hack a social network, Because despite the fact that these platforms have high security barriers, it is always possible to observe a flaw, through which windows are opened to be able to violate them and thus hack them.

And this is something that spy apps, amend known as Keyloggers They are taken advantage of, since through their right installation they let the hacker to admission all the information that is registered on the screen or keyboard of the device where it is located, such as, for example, the passwords to the different social networks of a victim, thus reaching to hack it.
With the assistance of a Keylogger you lot tin can really admission any social network, some of the almost popular and easy to use are:
Hack with Keyloggers
With keylogger.store You will become more powerful and avant-garde spying functions on the market place, since with its keylogger function it allows yous to remotely monitor all the keystrokes made on the target phone and computer.
Thus, beingness able to capture all the entry information of the unlike social networks with which your victim interacts.
This is one of the nearly reliable methods of knowing what the person in question is typing on their telephone and this is how information technology works:
Other methods to hack social networks
Do you want to catch your cheating partner? Or exercise you want to monitor your child's online activity? The good news is that there are several techniques you can use to achieve this. Here are some of them.

How to hack social media using the forget password feature
This is i of the nigh forgotten simply efficient methods to hack an account of whatsoever social network if you lot accept physical access to the target'south telephone and electronic mail, you just accept to follow the following steps:
- Enter the application of the social network you want to hack and click on Forgotten access data to reset the password.
- A secret code will exist sent to your victim's phone, so you lot must have it with you at all times, re-create the lawmaking and delete the message then as not to leave traces.
- Enter the code in the application to admission the account and voila, you can kickoff spying on all the content stored in that social network.
How to discover the password of a social network through spider web pages.
Currently, information technology is not necessary to have technical cognition in calculator scientific discipline to hack a social network, considering there are specialized social network hacking software that does all the work for yous. This being the case for the different web pages dedicated to violating the account of the user you desire.
Since this is 1 of the easiest online methods to hack you just have to:
- Search in your web browser passwords saved in google
- Login with the gmail account where the passwords are stored
- Notice if Facebook, Instagram, TikTok or other means take the password saved
- Once the requested data has been located and analyzed, you will only have to copy them and enter the social network of your victim.
Many users consider social networks to be safe, and think that their accounts and personal information are always protected, which is why every day they enter a lot of confidential data to access their accounts.
If, on the other hand, yous exercise non have a practiced reason to carry out these acts, information technology is best to put the idea aside, or make sure that your actions comply with the conditions of use and the terms of the services.
Loading comments...
Source: https://accountweb.is/
0 Response to "Stalkers People You May Know Facebook"
Post a Comment